Navigating the Tides of Cybersecurity: Trends and Insights (22nd - 28th Jan 2024)

Introduction
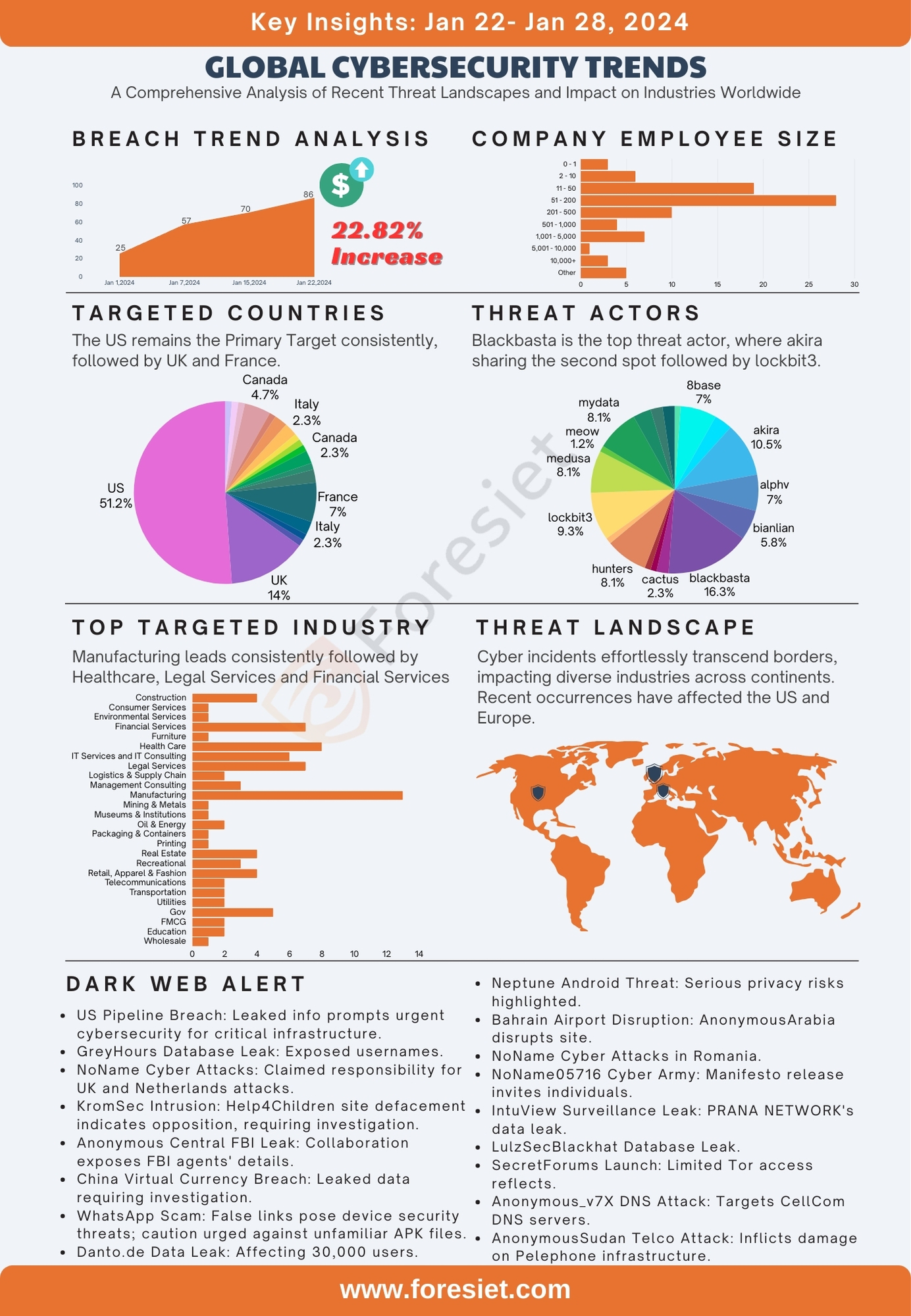
The percentage of increase this week is a noteworthy 22%, underscoring the dynamic nature of the cybersecurity landscape. In the ever-evolving realm of cybersecurity, understanding the Global Targets and threat landscape is paramount. Our analysis delves into the data, revealing a concentration of cyber targeting predominantly focused on the United States, underlining the urgent need for robust cybersecurity measures on a global scale. As we explore Industry Dynamics and Employee Size, the multifaceted nature of cyber threats becomes apparent, urging businesses to remain adaptive. The assessment on Attack Surface Management unveils vulnerabilities, highlighting the critical importance of proactive security measures. Lastly, we delve into the intriguing world of Threat Actors, where sophisticated groups demand heightened vigilance and tailored strategies.
Global Targets
The data reveals a notable concentration of cyber targeting, with the United States emerging as the primary focus, comprising approximately 54.32% of the total instances. Following closely are the United Kingdom (14.81%) and France (7.41%), indicating a persistent and strategic interest of threat actors in these nations. Canada also features prominently, accounting for 4.94% of instances and emphasizing its significance as a target. Other countries such as Israel, Italy, and China are subject to targeting, albeit to a lesser extent, collectively representing around 6.17% of the instances. This data underscores the urgent need for robust cybersecurity measures on a global scale, particularly for nations consistently in the crosshairs of cyber threats.
It is noteworthy that India, despite being in the top 3 targets last week, has now shifted to the 12th place. This dynamic shift underscores the dynamic nature of cyber threats and highlights the importance of agile and adaptive cybersecurity strategies to address evolving patterns of targeting.
Industry Dynamics
Manufacturing emerges as the foremost leader in the dynamic landscape of industries, constituting approximately 16.05% of the total instances. Following closely, the healthcare sector establishes a substantial presence with 9.88%. Legal Services and Financial Services emerge as active contributors, representing 8.64% of the instances. Further exploration reveals diverse sectors such as Construction, IT Services, and Real Estate, collectively shaping 26.79% of the nuanced fabric of industry engagement. This data underscores the importance of adaptability and strategic insights for businesses navigating this dynamic terrain.
As industries interweave, the data also highlights the evolving nature of industry participation, urging businesses to remain attuned to emerging trends. The imperative to seize growth opportunities is evident, reinforcing the need for a proactive approach in this ever-changing business ecosystem. In this context, leveraging comprehensive industry insights becomes pivotal for organizations aiming to stay competitive and responsive to the demands of the contemporary business landscape.
Employee Size Matters
In scrutinizing the data concerning company employee size, a nuanced understanding of organizational structures comes to the forefront. The distribution reveals a diverse landscape, with 51 - 200 employee-sized companies emerging as the most prevalent category, boasting 28 instances. Subsequently, companies with 11 - 50 employees follow closely with 19 instances, underlining the prevalence of mid-sized enterprises. Notably, a significant number of companies fall within the range of 2 - 10 employees, constituting 6 instances, emphasizing the prevalence of smaller businesses in the dataset.
A closer examination of larger enterprises reveals that companies with employee sizes ranging from 201 to 500 and 1,001 to 5,000 also command a notable presence, with 10 and 7 instances, respectively. Furthermore, a distinctive representation of larger corporations, those with 10,000 or more employees, underscores the presence of sizable organizations within the dataset. The classification of 'Other' with 5 instances further adds to the complexity, indicating a subset of companies with unique or unspecified employee sizes. In essence, this comprehensive analysis sheds light on the multifaceted nature of organizational sizes and their significance in the broader business landscape.
Analysis on Attack Surface Management
This week's security assessment reveals the identification of 494 vulnerabilities, with 29 classified as critical vulnerabilities. Among the critical vulnerabilities, 26 currently have publicly available exploits. Notably, 1 vulnerability exhibit an EPSS score ranging from 0.04% to 0.15%, indicating a High Level of Potential Exploitation.
The Foresiet research team has diligently identified exploits available for Opportunistic Threat actors, specifically targeting vulnerabilities thatfacilitate easy attacks. A few notable vulnerabilities in this context include CVE-2024-22895, CVE-2024-0204, CVE-2023-7227, CVE-2024-0204, CVE-2024-0402, CVE-2024-21326, CVE-2024-22205, CVE-2024-23621, and more. This proactive identification and disclosure aim to raise awareness and prompt necessary security measures to mitigate potential risks associated with these vulnerabilities
Threat Actors
The analysis of threat actors unveils a nuanced landscape characterized by varying levels of sophistication and impact. At the forefront is 'blackbasta,' constituting approximately 18.92% of the instances, indicating a persistent and formidable threat. Following closely are 'akira' and 'lockbit3,' representing 12.74% and 11.11% of instances, respectively, showcasing a significant and consistent threat presence. These groups demand heightened vigilance and tailored security strategies to counter potential breaches effectively.
In the mid-tier, 'alphv' exhibits substantial activity, constituting 9.52% of instances, underscoring the need for proactive cybersecurity measures to counter evolving tactics. 'Hunters,' representing 11.11% of instances, represents a substantial threat, prompting organizations to stay vigilant and agile in their security approaches.
Top 5 Threat Actors
- Blackbasta (18.92%): Renowned for their highly active and persistent threat campaigns, Blackbasta poses a formidable challenge to cybersecurity. Their sophisticated tactics demand the implementation of robust defensive measures and continual monitoring to safeguard against potential breaches. Organizations facing this threat actor should prioritize advanced threat intelligence and proactive security strategies.
- Akira (12.74%): Akira consistently exhibits substantial and persistent threat activity, necessitating heightened vigilance from targeted entities. Understanding their modus operandi and evolving tactics is crucial for organizations looking to enhance their security posture. Regular threat assessments and continuous monitoring are imperative to effectively thwart potential attacks orchestrated by Akira.
- Lockbit3 (11.11%): Lockbit3 showcases a noteworthy level of threat sophistication, emphasizing the critical need for fortified defenses. Organizations should focus on adopting multi-layered security protocols, including advanced endpoint protection and robust encryption mechanisms. Regular security audits and threat simulations can aid in identifying and addressing vulnerabilities targeted by Lockbit3.
- Alphv (9.52%): Alphv's substantial activity underscores the importance of proactive cybersecurity measures. Organizations dealing with Alphv should invest in threat hunting capabilities and collaborative threat intelligence sharing to stay ahead of this group's evolving tactics. Additionally, fostering a culture of cybersecurity awareness among employees becomes pivotal in mitigating risks associated with Alphv.
- Hunters (11.11%): As a significant threat actor, Hunters require organizations to stay vigilant and agile in their security approaches. Continuous threat intelligence updates and collaboration with cybersecurity communities are essential to anticipate and counteract the evolving strategies employed by Hunters. Implementing robust incident response plans is crucial to minimize the potential impact of attacks orchestrated by this threat group.
This comprehensive analysis provides a detailed overview of the threat landscape, emphasizing the multifaceted nature of threat actors and the importance of a percentage-driven, comprehensive, and adaptive security approach.
Recent Threats in the Dark Web Community
A series of alarming cybersecurity threats has surfaced on the dark web, with threat actors targeting critical infrastructure and entities globally. Noteworthy incidents include a breach affecting major pipeline and energy companies in the United States, exposing sensitive information and emphasizing the urgent need for heightened cybersecurity measures. Additionally, threat groups such as NoName and CyberDragon have claimed responsibility for cyber attacks on government websites, raising concerns about potential data breaches and service disruptions. The proliferation of forums like "SecretForums" underscores the evolving nature of illicit online platforms, posing challenges for monitoring and addressing emerging cyber threats. These incidents highlight the intersection of cyber threats with geopolitical tensions, emphasizing the critical importance of robust cybersecurity strategies for safeguarding sensitive information and essential services. Authorities are expected to intensify investigations and mitigation efforts in response to these dark web cybersecurity challenges.
- A threat actor has exposed sensitive information from major U.S. pipeline and energy companies, including PGP passwords and keys, raising serious security concerns for the critical infrastructure. The breach extends to the dark web, emphasizing the need for urgent cybersecurity measures.
- GreyHours, a targeted entity, faced a significant breach with leaked data encompassing usernames, encrypted passwords, and other personal information. The threat actor claims to have shut down the GreyHours website, necessitating enhanced cybersecurity defenses and ongoing investigations.
- NoName, a threat actor group, asserts responsibility for cyber attacks on prominent UK websites, including trade organizations and local councils. The potential for data breaches and service disruptions highlights the importance of robust cybersecurity measures across diverse sectors.
- NoName, implicated in cyber attacks, claims responsibility for disrupting Dutch entities amidst military aid to Ukraine. Alleged targets include public transportation, tax administration, and information portals, prompting investigations to secure critical infrastructure.
- KromSec hacks a Western foundation, expressing opposition to perceived corruption and injustice. The group defaces the Help4Children homepage, prompting authorities to investigate and assess potential implications for cybersecurity.
- "Anonymous Central" collaborates with "RHA R" to claim the acquisition of personal information from all FBI agents in the U.S. The leaked document poses serious security concerns, highlighting challenges in safeguarding sensitive information.
- A China virtual currency exchange experiences a data leak affecting 1 million users. The incident underscores the need for robust cybersecurity measures to protect user information, prompting investigations and risk mitigation actions.
- Users are warned of a new WhatsApp scam involving APK files falsely linked to the Ram Mandir inauguration, posing potential threats to device security. Vigilance against installing files from unknown sources is advised.
- The Neptune Android Remote Control, a sophisticated threat, compromises user privacy with invasive features, necessitating caution and robust security practices from users.
- NoName057(16) disrupts Romanian internet sites in response to geopolitical statements, prompting investigations into the source and impact of the cyber disruptions.
- Germany-based shopping website Danto.de reports a data breach affecting 30,000 users, emphasizing the importance of heightened cybersecurity measures and user vigilance.
- Bahrain Airport faces disruption by anonymousArabia, protesting against Bahrain's alleged support for Israel and military actions in Yemen, reflecting ongoing geopolitical tensions.
- CyberDragon claims to breach the European Parliament servers, escalating tensions with warnings to disrupt projects perceived as anti-Russian. The incident highlights geopolitical cyber activities and the need for heightened cybersecurity.
- Romanian websites fall victim to a cyber attack by "noname," prompting investigations into the motive and extent of the incident, highlighting challenges in safeguarding government digital infrastructure.
- NoName05716 releases an updated manifesto, advocating harm to Russia's adversaries and growing membership, underscoring the intersection of cyber threats with geopolitical interests.
- PRANA NETWORK exposes information on the Israeli surveillance system provided by IntuView, raising privacy concerns and highlighting potential risks associated with mass-scale data analysis.
- Anonymous Collective takes down Egypt national airline's website in protest of the government's refusal to permit humanitarian aid into Gaza, showcasing cyber actions as a form of political protest.
- LulzSecBlackhat claims responsibility for a database leak targeting the largest hotels in Israel, emphasizing ongoing challenges in securing sensitive information online.
- A new forum, "SecretForums Propaganda," is set to launch, replacing blackforums, highlighting the evolving nature of illicit online forums and persistent challenges in addressing emerging cyber threats.
- Anonymous_v7X orchestrates a significant cyberattack on CellCom's DNS servers, posing risks to Israel's telecommunications infrastructure and prompting investigations into the potential impact.
- AnonymousSudan launches a severe cyberattack on Pelephone Communications Ltd, tying the incident to perceived Israeli actions in Gaza and raising concerns about collateral damage to critical infrastructure.
Conclusion
In conclusion, this comprehensive analysis provides a panoramic view of the current cybersecurity landscape. The Global Targets highlight the persistent nature of cyber threats, emphasizing the importance of a global, adaptive approach. Industry Dynamics and Employee Size shed light on the intricate fabric of businesses, urging organizations to stay competitive. The Analysis on Attack Surface Exposure and Threat Actors showcases the critical need for proactive security measures and continuous vigilance in the face of evolving cyber threats. As we navigate this complex terrain, the call for cybersecurity awareness and adaptive strategies becomes more pronounced than ever.
About Foresiet!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


June 7, 2024, 7:02 p.m.

May 23, 2024, 8:02 p.m.