Navigating the Tides of Cybersecurity: Trends and Insights (Februrary 26th - March 3rd, 2024)

Introduction
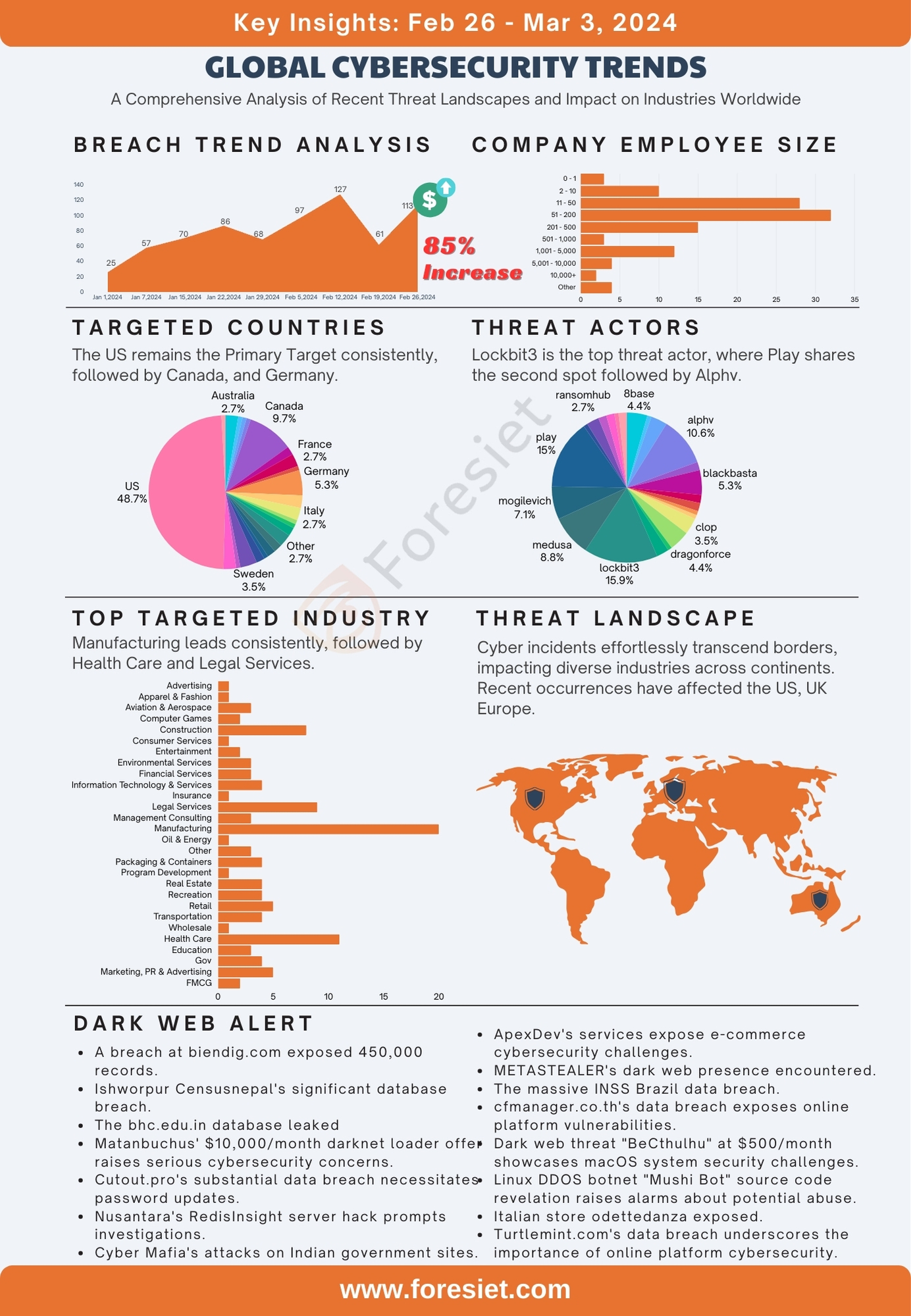
In the rapidly evolving digital landscape, the escalating frequency and sophistication of cyber threats pose a collective challenge to nations across the globe. The surge of 113 reported breaches underscores the pressing need for enhanced cybersecurity measures in this interconnected era. The focal point often centres on the United States, with 55 incidents highlighting the urgency for robust defences. However, cybersecurity challenges span diverse nations such as Canada, Germany, and Australia, emphasizing the imperative for collaborative efforts and international cooperation to achieve global targets. This introduction sets the stage for a comprehensive exploration of breach data, industry dynamics, the correlation between employee size and vulnerabilities, attack surface management, threat actors, and dark web threats, offering insights into the multifaceted landscape of cybersecurity.
Global Targets
In an era marked by interconnected technologies, the surge in cyber threats poses a collective challenge to nations globally, with 113 reported breaches underscoring the pressing need for enhanced cybersecurity measures. The United States, at the forefront with 55 incidents (48.7%), highlights the urgency for robust defences, emphasizing the necessity of collaborative efforts. While the focus often centre's on the U.S., cybersecurity challenges span diverse nations such as Canada, Germany, and Australia. Achieving global targets in cybersecurity demands a united front, transcending borders and fostering international cooperation.
Unsurprisingly, the United States stands as the epicentre of cyber breaches, accounting for 48.7% of total incidents. This emphasizes the colossal challenge of fortifying digital defences against evolving threats, impacting not only national security but also the integrity of private and public sector data. Simultaneously, Canada, with 11 breaches (9.7%), highlights the need for reinforced cybersecurity frameworks to protect sensitive information and critical systems. Both nations underscore the imperative for a collaborative and proactive approach to cybersecurity, essential for building a resilient global defence against the ever-growing threat landscape.
Industry Dynamics
This week, the breach data reveals a detailed picture of cybersecurity challenges across various industries, totalling 113 incidents. Manufacturing takes centre stage, comprising approximately 17.7% of the total breaches. The sector's vulnerability underscores the critical need for heightened cybersecurity measures to protect both intellectual property and essential infrastructure. Simultaneously, the Construction industry and Legal Services face significant challenges, emphasizing the importance of safeguarding sensitive information within these domains.
Health Care contributes around 9.7% to the total incidents, while the Education sector accounts for approximately 2.7%. These statistics underscore the widespread impact on industries crucial to societal well-being. As breaches continue to affect sectors integral to the functioning of economies, urgent and collaborative efforts are imperative to fortify cybersecurity frameworks across the board. This week's breach analysis highlights the necessity for a proactive and united approach to address the evolving threat landscape in an increasingly interconnected digital environment.
Employee Size Matters
The correlation between an organization's employee size and its vulnerability to cybersecurity breaches is unmistakable. Analyzing the data reveals that organizations with 51 to 200 employees experience the highest percentage of breaches, accounting for approximately 28.3% of the total 113 incidents. This significant figure underscores the unique challenges faced by mid-sized enterprises in maintaining robust cybersecurity measures. Meanwhile, smaller organizations with 11 to 50 employees also exhibit a notable vulnerability, constituting approximately 24.8% of the breaches. Together, these two categories make up more than half of the total breaches. The prevalence of breaches in these smaller to mid-sized entities suggests a critical need for tailored cybersecurity strategies to address their specific risks and ensure the protection of sensitive information.
Conversely, larger organizations, particularly those with over 10,000 employees, show a comparatively lower percentage of breaches, totalling only about 1.8% of the incidents. This indicates that while larger enterprises may have more extensive resources to dedicate to cybersecurity, they are not immune to threats. As the Grand Total of breaches stands at 113, these findings underscore the necessity for organizations of all sizes to prioritize cybersecurity measures tailored to their unique operational landscapes. Recognizing the impact of employee size on cybersecurity vulnerabilities is paramount in fostering a holistic approach to data protection across diverse organizational structures.
Analysis on Attack Surface Management
This week, our scrutiny of digital landscapes uncovered a total of 1008 vulnerabilities, marking 28 of them as critical. Within this critical subset, 482 vulnerabilities raise concern, and notably, 2 of them currently possess publicly available exploits. Noteworthy is the fact that both these vulnerabilities are assigned an EPSS score ranging from 0.04% to 0.09%, indicating a High Level of Potential Exploitation.
The Foresiet research team has diligently pinpointed exploits accessible to opportunistic threat actors, targeting vulnerabilities that present an easy attack surface. Some of the identified exploits include CVE-2024-27298, CVE-2024-25925, CVE-2024-25913, CVE-2024-25909, CVE-2024-1403, CVE-2024-0455, and others. This revelation underscores the critical importance of proactively addressing these vulnerabilities to mitigate potential threats and fortify our digital defenses against emerging risks.
Threat Actors
This week's cybersecurity landscape highlights a diverse range of threat groups, each leaving its mark on digital security. Notably, the Lockbit3 group stands out with a substantial 18 breaches, showcasing a sophisticated and persistent threat. Following closely is the Play group, contributing 17 breaches, emphasizing the need for vigilant measures against their activities. Alphv and Medusa groups also warrant attention, with 12 and 10 breaches respectively, signifying persistent challenges posed by these entities.
In terms of percentages, Lockbit3 constitutes a significant portion, accounting for approximately 15.9% of the total breaches. Play follows closely, representing around 15%, while Alphv and Medusa contribute 10.6% and 8.8% respectively. These percentages underscore the dynamic nature of cyber threats posed by distinct groups, urging organizations to tailor their cybersecurity strategies to effectively counter the specific methodologies employed by each threat actor. As the Grand Total of breaches stands at 113, this summary highlights the diverse and evolving threat landscape organizations must navigate to safeguard their digital assets effectively.
Top 5 Threat Actors
- Lockbit3 (15.9%): Lockbit3 stands out as a formidable threat actor, accounting for a significant 15.9% of the total breaches. Known for its sophisticated cyber operations, this group employs advanced tactics, techniques, and procedures (TTPs) to infiltrate systems, demonstrating a high level of expertise in executing targeted cyber-attacks.
- Play (15%): Play is a prominent threat actor contributing to 15% of the total breaches, showcasing a substantial impact on our digital security. This group is characterized by its dynamic and evolving strategies, leveraging innovative approaches to exploit vulnerabilities and compromise sensitive information.
- Alphv (10.6%):Alphv emerges as a noteworthy threat actor, constituting around 10.6% of the total breaches. Known for its calculated and precise cyber activities, Alphv demonstrates a keen understanding of the evolving threat landscape, making it a formidable entity in the cybersecurity domain.
- Medusa (8.8%):Medusa is a significant threat actor contributing to approximately 8.8% of the total breaches. This group is characterized by its strategic and multifaceted approach, targeting vulnerabilities across various sectors with a focus on maximizing the impact of its cyber operations.
- Mogilevich (7.1%): Mogilevich is a notable threat actor, responsible for around 7.1% of the total breaches. Known for its persistent and adaptable tactics, this group demonstrates a capacity to exploit vulnerabilities effectively, emphasizing the importance of robust cybersecurity measures to counter its activities.
Dark web threats:
The recent surge in cybersecurity incidents highlights the pervasive and evolving threats across various sectors. Notable breaches include the compromise of biendig.com, exposing 450,000 records, raising concerns in the digital service industry. Educational institutions, as seen with bhc.edu.in, face security challenges, emphasizing the need for enhanced measures. Dark web developments showcase the emergence of sophisticated tools like the Matanbuchus 2.0 Private Resident Loader, posing significant risks for cybercriminal activities. Meanwhile, Team Cyber Mafia's successful attacks on Indian government websites underscore the impact on essential services. The rise of ApexDev targeting e-commerce platforms and the discovery of METASTEALER on the dark web further demonstrate the escalating sophistication of cyber threats. Government institutions, as evident in Brazil's National Social Security Institute, and businesses like cfmanager.co.th and odettedanza.it face critical data breaches, emphasizing the imperative for robust cybersecurity practices. The disclosure of the source code for the Linux DDOS botnet "Mushi Bot" raises alarms about potential widespread abuse. Lastly, the compromise of Turtlemint.com underscores the vulnerability of online platforms, necessitating urgent investigations and strengthened cybersecurity measures to safeguard user data and privacy.
- On February 25, 2024, biendig.com, a website specializing in professional services for tailored digital presences, experienced a significant data breach, exposing approximately 450,000 records stored in a SQL file totalling 803MB. The compromised database includes sensitive user information such as User IDs, titles, credentials (usernames and passwords), registration details, contact information (phone numbers, email addresses), account statuses, verification statuses, and additional personal data. The breach raises concerns regarding the security of user information on the platform and emphasizes the need for heightened cybersecurity measures in the digital service industry.
- On November 22, 2023, a substantial data breach occurred within the Ishworpur Censusnepal database, affecting 1,03,0263 lines of data. The compromised information encompasses sensitive details regarding households and their members, including names, genders, dates of birth, caste, religion, education levels, occupations, marital statuses, and health conditions. The breached database comprises two primary tables, detailing household and member information. The incident poses significant privacy concerns and underscores the importance of reinforcing data security in census databases to safeguard citizens' sensitive information.
- On February 25, 2024, the bhc.edu.in database experienced a significant security breach, exposing sensitive personal information of individuals associated with Bishop Heber College (BHC) in Tiruchirappalli, Tamil Nadu, India. The breached data, leaked on a notorious hacking forum by the group "Anonymous World," encompasses details of faculty, staff, and students at Bishop Heber College. Notable compromised information includes names, contact details, academic departments, roles, and other relevant data. The exposed entries feature email addresses, phone numbers, academic disciplines, and affiliations within the college. This incident underscores the critical need for enhanced cybersecurity measures to protect the privacy and personal information of educational institutions and their stakeholders.
- In a recent darknet development, the notorious vendor Matanbuchus, self-styled as a "darknet demon," has emerged with a tempting proposition for cybercriminals seeking advanced tools. Matanbuchus is now offering the rental of the Matanbuchus 2.0 Private Resident Loader, showcasing a host of powerful features for potential clients. The darknet profile of Matanbuchus, adorned with Premium membership status and a history dating back to December 29, 2018, reveals the rental price for the resident loader at an exorbitant $10,000 per month. Limited to just three spots, the offer comes with the allure of comprehensive functionality and a proprietary morpher, posing a significant concern for cybersecurity authorities.
- Cutout.pro is reeling from a substantial data breach that has exposed over 20 million user records. Unearthed by cybersecurity experts, spearheaded by KryptonZambie, the breach involves the compromise of sensitive information, including emails and passwords. Users are strongly advised to promptly update their passwords, underscoring the critical need for robust online security measures to mitigate potential risks stemming from the breach.
- "The RedisInsight server in India fell victim to a cyber intrusion orchestrated by the hacking group Nusantara, resulting in the exposure of user data. Renowned for its graphical interface for Redis, RedisInsight faced a breach that compromises user privacy. The leaked data encompasses user information, prompting concerns about potential misuse and unauthorized access to sensitive details. In a message, Nusantara expressed solidarity with Muslim hackers and emphasized support for the Palestinian cause. Authorities are actively investigating the breach, urging affected users to exercise vigilance and take necessary precautions in response to this security incident.
- Team Cyber Mafia has launched a series of cyber attacks, successfully taking down official websites of key Indian government institutions, including the Ministry of Youth Affairs & Sports (sportsauthorityofindia.nic.in), the Indian Navy (indiannavy.nic.in), and the National Human Rights Commission of India (nhrc.nic.in). The attacks have rendered these websites inaccessible, disrupting access to essential services. Team Cyber Mafia has substantiated their actions by sharing check-host reports, emphasizing the urgency for authorities to address the breaches and restore the affected websites promptly.
- A cybercriminal entity identified as ApexDev has recently come to light, offering illicit services geared towards intercepting sensitive data from online shops. With operations dating back to June 2023, this group specializes in deploying sniffers on e-commerce platforms, aiming to extract valuable information for their nefarious purposes. The emergence of ApexDev raises concerns about the security vulnerabilities within online shopping platforms and underscores the ongoing challenges posed by cyber threats in the digital landscape.
- A concerning development in the realm of cybercrime reveals the emergence of METASTEALER, an advanced desktop panel equipped with a myriad of illicit functionalities. Promoted through a Telegram bot, METASTEALER touts a range of features specifically crafted to facilitate data theft and exploitation. The discovery of this sophisticated tool underscores the evolving landscape of cyber threats, emphasizing the need for heightened cybersecurity measures to counteract such advanced tools employed by malicious actors.
- In a significant and alarming revelation, a massive data breach has unfolded at the National Social Security Institute (INSS) of Brazil, affecting approximately 879,492 individuals. The exposed data encompasses highly sensitive information, including social security numbers (CPF), names, dates of birth, city and state details, as well as banking information and benefit values. This breach raises serious concerns about the security of personal data within governmental institutions and underscores the imperative for robust cybersecurity measures to safeguard citizens' privacy and prevent unauthorized access to sensitive information.
- A notable data breach has been disclosed at cfmanager.co.th, a social live sales support company, leading to the compromise of databases containing records from over 5000 online shop sellers. The exposed data involves sensitive information, including seller social tokens, customer details, and other associated records. This incident underscores the vulnerability of online platforms and highlights the importance of stringent cybersecurity measures to protect the integrity and privacy of user data within e-commerce environments.
- In a recent dark web discovery, a new threat has emerged as cybercriminals introduce the sophisticated macOS stealer "BeCthulhu" for sale. Priced at $500 per month, this malicious tool exhibits a diverse set of capabilities tailored to infiltrate and extract sensitive data from Apple devices operating on macOS. The presence of such advanced threats underscores the ongoing challenges in securing macOS systems and emphasizes the critical need for heightened cybersecurity measures to counteract evolving threats in the digital landscape.
- In a concerning development on the dark web, cybercriminals have unveiled the source code for the Linux DDOS botnet named "Mushi Bot." Demonstrating advanced features for malicious activities, this botnet stands out for its distinctive capabilities. Operated through CNC servers and a fallback domain method, Mushi Bot goes beyond conventional malicious purposes, showcasing a level of sophistication that poses significant challenges for cybersecurity. The disclosure of its source code raises alarms about potential widespread abuse and emphasizes the ongoing need for robust defenses against evolving threats in the Linux ecosystem.
- A concerning data breach has come to light at the Italian women's clothing store, odettedanza.it. The breach, disclosed by a data seller named "Spoofer," has exposed sensitive customer information, sparking apprehensions regarding the website's data security. The leaked sample data encompasses a range of personal details, including ID, name, surname, email, city, province, country, postal code, address, phone, cellular information, user ID, street number, and additional details. This incident underscores the pressing need for robust cybersecurity measures to protect customer data and maintain the trust of online consumers.
- A notable data breach has been reported involving the Indian insurance aggregator website, Turtlemint.com. Disclosed by the user "taplonaroda," the breach has compromised sensitive information belonging to approximately 1.8 million individuals. This incident highlights the vulnerability of online platforms and underscores the critical importance of implementing robust cybersecurity measures to safeguard user data and prevent unauthorized access. Authorities are urged to investigate the breach promptly to mitigate potential risks and ensure the privacy and security of affected individuals.
Conclusion
As we navigate the intricate landscape of cybersecurity, the data reveals a complex web of challenges across industries, organizational sizes, and global regions. The breach analysis sheds light on the vulnerabilities faced by nations and industries, emphasizing the critical need for collaborative and proactive cybersecurity measures. From the impact on manufacturing, construction, legal services, health care, and education to the correlation between employee size and breaches, it becomes evident that a tailored and holistic approach is essential. The scrutiny of attack surface management unveils vulnerabilities that demand immediate attention, while the diverse threat actors underscore the dynamic nature of cyber threats. Dark web developments and notable breaches highlight the imperative for organizations to fortify their digital defences. In conclusion, this exploration serves as a call to action for nations, industries, and organizations to unite in the pursuit of robust cybersecurity frameworks, fostering resilience against the ever-evolving threat landscape.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


June 7, 2024, 7:02 p.m.

May 23, 2024, 8:02 p.m.