Navigating the Tides of Cybersecurity: Trends and Insights (28th Jan - 4th Feb 2024)

Introduction
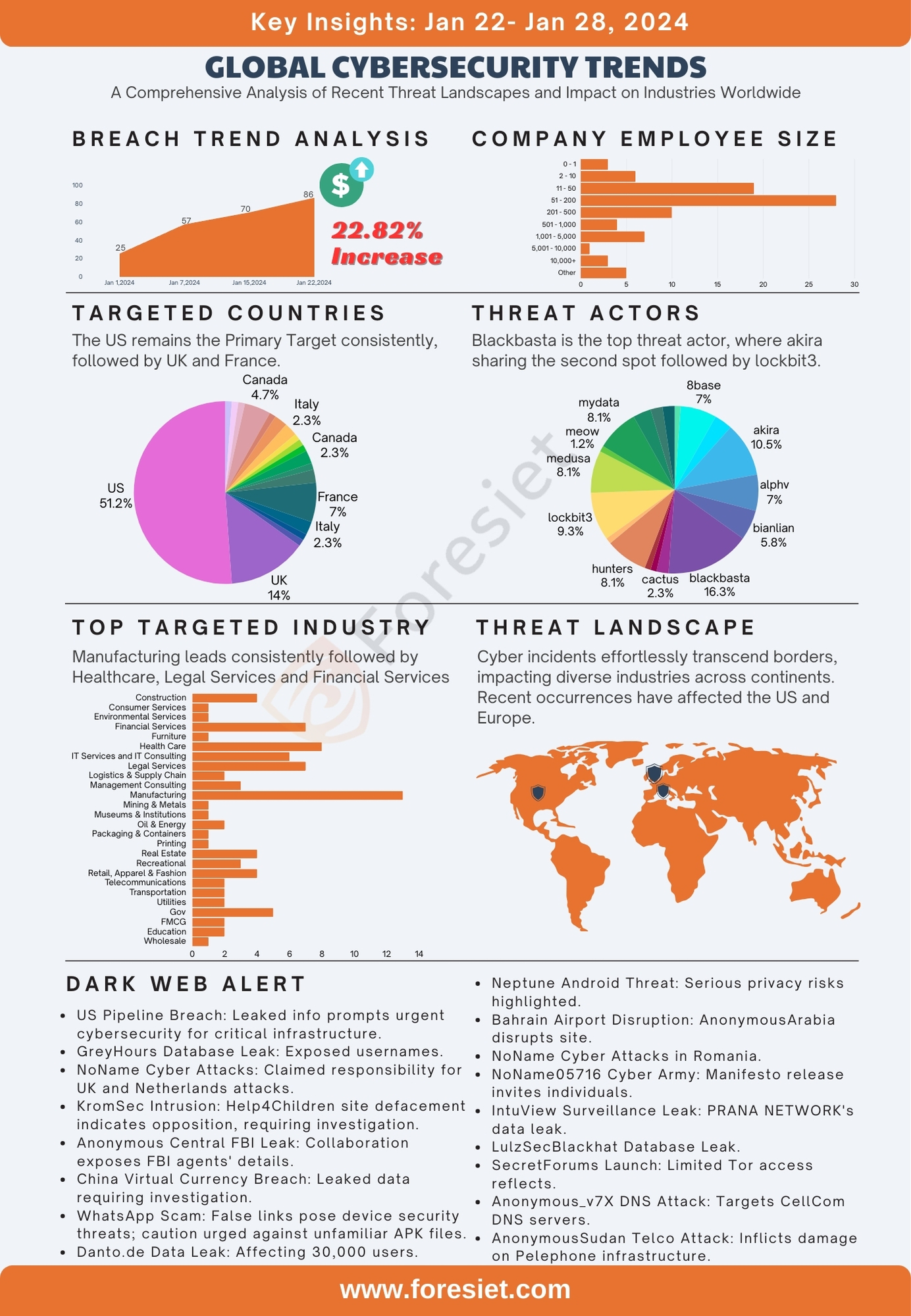
In a dynamic landscape of cybersecurity, the past week has witnessed a notable 20.93% decrease in threats, offering a brief respite from the relentless tide of digital vulnerabilities. A striking trend has emerged, revealing a shift in targeting dynamics—while the manufacturing sector remains a consistent focus, law firms have unexpectedly found themselves under keen scrutiny, emerging as the most breached entities. Amidst this evolving threat landscape, the notorious Lockbit3 continues to assert its dominance as a major threat actor, perpetuating its impact across diverse sectors. Further amplifying the urgency, companies within the employee size range of 51-200 have faced substantial threats, underscoring the significance of tailored cybersecurity measures for entities of this scale. This blog explores the nuances of these recent developments, providing insights into the evolving nature of cyber threats and their impact on various sectors and company sizes.
Global Targets
In the complex landscape of global threats, the United States takes a commanding lead in the global cybersecurity arena, representing a substantial 57.63% of reported breaches for the week. This statistic not only underscores the nation's technological resilience but also highlights its commitment to transparency in addressing cybersecurity threats. Contributing 10.17% collectively, France and the United Kingdom play crucial roles in the European front of cybersecurity, emphasizing the significance of regional collaboration in mitigating global digital risks.
Examining the top 5 countries reveals a collaborative and diverse global effort in monitoring and responding to cybersecurity threats. The combined efforts of the U.S., France, the UK, Australia, Mexico, and Italy (each at approximately 5.08%) showcase a unified response to the evolving landscape of digital security, emphasizing the importance of shared intelligence and strategic cooperation in mitigating the complex challenges posed by cyber threats.
Industry Dynamics
Examining recent breach data reveals patterns across various industries, shedding light on the current cybersecurity landscape. Not surprisingly, Manufacturing emerges as the most affected sector, representing a substantial 17.39% of reported breaches. This persistent vulnerability underscores the ongoing challenges faced by the manufacturing industry, which is consistently under attack, highlighting the urgent need for heightened and adaptive security measures.
Legal Services and Construction closely follow, each contributing 15.94% of breaches. This shared vulnerability emphasizes the critical importance of cybersecurity resilience, especially in sectors dealing with sensitive information and large-scale projects. The prominence of these sectors in breach occurrences suggests a concerted effort is necessary to fortify their digital defenses.
In addition, Healthcare, constituting 10.87% of breaches, faces persistent challenges in securing sensitive data. Information Technology & Services and Transportation, each contributing 8.7% of breaches, underscore the broad spectrum of industries susceptible to cybersecurity threats. This diverse array of affected sectors emphasizes the need for tailored security measures to address specific vulnerabilities and protect against the ever-evolving landscape of cyber threats.
Employee Size Matters
Analyzing recent breach data reveals nuanced insights into the correlation between company size and cybersecurity incidents. Companies with 51 to 200 employees constitute a substantial 37.74% of reported breaches, suggesting potential gaps in security measures for mid-sized enterprises that may require targeted attention. Small-sized companies with 11 to 50 employees follow closely, contributing significantly with 32.08% of the overall breach count, underscoring the importance of addressing cybersecurity challenges for smaller entities. Resource constraints and evolving threat landscapes may necessitate tailored solutions to fortify the digital defenses of these businesses.
Larger enterprises, specifically those with 201 to 500 employees and 501 to 1,000 employees, collectively account for 13.21% of breaches. While larger companies are not immune, their size may afford them additional resources to invest in comprehensive cybersecurity infrastructure. However, the analysis prompts a closer examination of potential variations in security practices within these larger entities. The challenges faced by very small companies (2 to 10 employees) and those falling into the 'Other' category, contributing 12.26% and 7.55% of breaches, respectively, highlight the necessity of recognizing unique cybersecurity needs across various company sizes for developing effective strategies against a diverse range of cyber threats. This multifaceted analysis urges industry stakeholders to tailor cybersecurity initiatives, acknowledging the specific dynamics inherent in companies of different sizes.
Analysis on Attack Surface Management
This week, our analysis revealed a total of 530 vulnerabilities, with 50 classified as critical. Within these critical vulnerabilities, 20 currently possess publicly available exploits. Notably, all 20 vulnerabilities carry an EPSS score ranging from 0.04% to 6.57%, indicating a High Level of Potential Exploitation.
The Foresiet research team has identified exploits available for Opportunistic Threat actors, specifically targeting easy attack vectors. Some of these vulnerabilities include CVE-2024-23652, CVE-2023-49617, CVE-2023-47143, CVE-2024-0996, CVE-2024-0995, CVE-2024-0994, CVE-2024-0993, CVE-2024-0992, CVE-2024-0991, CVE-2024-0990, CVE-2024-0986, etc. This heightened exposure underscores the critical need for immediate attention and remediation efforts to secure potential weak points in the system.
Threat Actors
In our recent cybersecurity analysis, we've identified and categorized various threat actor groups, each presenting unique challenges and potential risks to digital security. The landscape is dynamic, with several noteworthy groups exhibiting recurrent activities. Among them, 8base, Akira, Alphv, and Bianlian have emerged as key players, demanding specific attention and strategic responses due to their considerable impact.
The diverse nature of threat actor groups adds complexity to the current cybersecurity environment. These entities employ sophisticated tactics, underlining the need for organizations to stay ahead of evolving threats. Our analysis delves into the activities of these groups, shedding light on their potential motivations, attack methodologies, and preferred targets.
Top 5 Threat Actors
All the listed threat actors below have consistently posed significant threats, showcasing a persistent and ongoing challenge to digital security. Their recurrent activities underscore the need for vigilant monitoring, adaptive security measures, and proactive defensive strategies to effectively mitigate potential risks.
- 8base (Breach Percentage: 3.08%): Demonstrating consistent activity, 8base poses a substantial threat, necessitating focused mitigation efforts.
- Akira (Breach Percentage: 2.17%): With a discernible frequency, the Akira group demands heightened vigilance and targeted security strategies.
- Alphv (Breach Percentage: 2.17%): Exhibiting recurrent incidents, Alphv warrants careful monitoring and adaptive security measures.
- Bianlian (Breach Percentage: 2.61%): This group, with its considerable impact, requires thorough investigation and proactive response planning.
- Lockbit3 (Breach Percentage: 7.83%): Standing out with a significant impact, Lockbit3 demands immediate and comprehensive attention.
Incransom, with 5 incidents (2.17% breach percentage), signifies an ongoing challenge, reinforcing the importance of proactive defensive measures. These high-impact threat actors collectively represent a dynamic and evolving cybersecurity landscape, demanding constant scrutiny and adaptive security measures.
Recent Threats in the Dark Web Community
In a series of recent dark web threats, an unidentified actor exposed sensitive data from major US energy companies, while Anonymous Sudan orchestrated cyber assaults on Israeli hospital systems and targeted UAE-based airline FlyDubai. KromSec claimed responsibility for breaching India's Crime Research Investigation Agency, aligning with their opposition to an alliance with Israel. APT IRAN targeted Irancell, emphasizing concerns about organizational data security. Additionally, coordinated cyber-attacks by threat groups like Five Families and "noname" targeted entities globally, reflecting a dynamic and escalating landscape of cyber threats with geopolitical implications.
- Pipeline and Energy Data Breach: In a significant development, an unidentified threat actor exposed sensitive data from major pipeline and energy companies in the United States. The compromised information includes company names, PGP passwords, and keys. Simultaneously, the official website of the Egyptian Tax Authority faced a successful breach, attributed to the hacker group Anonymous Collective. This breach is allegedly in retaliation for Egypt's perceived slowdown of humanitarian aid to Gaza, reflecting the broader implications of cyber threats in the geopolitical landscape.
- Alliance for Russia: The ONF (People's Front) and Cyber Druzhina have formed an alliance with Anonymous Central, standing stronger together for Russia. This collaboration is emphasized with hashtags like #AnonymousSudan and #AnonymousCentral.
- Netherlands' Contribution and Cyber Response: The Netherlands joined the "IT Coalition," committing a 10 million euro contribution to enhance Ukraine's digital and cyber capabilities. In response, the hacker group "NoName057" targeted Dutch websites protesting their support for Ukraine's military efforts. The affected entities include OV-chipkaart, Municipality of Vlaardingen, and the Netherlands Revenue Authority's service portal. This incident highlights the global dynamics shaping cybersecurity collaborations.
- Anonymous Sudan Targets Israeli Hospitals: Anonymous Sudan executed a substantial cyber assault on interconnected hospital systems in Israel, resulting in considerable disruption. Over a thousand devices have been rendered completely disconnected, with potential for additional disruptions. These actions are a direct response to Israel's ongoing campaign in Gaza, and the group assumes responsibility for any resultant damage to Israel's health systems. It's imperative to acknowledge that hospitals in Gaza have similarly been targeted, underscoring the position against Israel's actions.
- KromSec's Responsibility in India: KromSec takes full responsibility for the recent breach of the Crime Research Investigation Agency of India. This action is a manifestation of their opposition to the agency's alliance with Israel, coinciding with their observance of Republic Day.
- Irancell Security Concerns: APT IRAN claims responsibility for the attack on Irancell, highlighting concerns about the security of its organizational data. The goal was not to blackmail Irancell, and some vulnerable systems are now inaccessible. Similar to SnappFood, the names of agents jeopardizing people's and organizations' data will be disclosed if Irancell does not address these individuals.
- NoName Targets Quantum-Systems: The assets of Quantum-Systems, a German drone manufacturer, have come under the focus of the NoName threat group. This targeting is in response to allegations that Quantum-Systems supplied drones to elements within the Ukrainian armed forces with reported neo-Nazi affiliations. Attention is also directed towards Germany and Lithuania.
- Five Families Cyber Attack: The cyberattack carried out by the threat group Five Families against Abelsantosyasoc.com.ar underscores the persistent threat posed by malicious actors in the digital domain. This incident highlights the critical importance of implementing robust cybersecurity measures and proactive threat mitigation strategies for organizations navigating the interconnected landscape of today.
- Unified Cyber Effort Against Finland: In an urgent development, a coordinated cyberattack has been initiated against Finnish authorities labeled as Russophobic. Notably, The National Cyber Army, 22C, PHOENIX, Federal Legion, UserSec, CyberDragon, and NETWORK (15) spearheaded this attack, targeting critical entities ranging from energy production and distribution companies to media outlets and public service portals.
- FlyDubai Cyber Attack: In a significant development, FlyDubai, a major UAE-based airline, has been targeted in a cyber attack by the threat group Anonymous Sudan. The assailants aimed at the airline's digital infrastructure, successfully disrupting critical components and causing a complete network outage. This attack resulted in the entire FlyDubai network being rendered inaccessible, including essential systems such as reservation and booking services, impacting users' ability to book flights.
- Melisron Israel Cyber Attack: Melisron Israel, a commercial real estate giant with a market capitalization of $3.46 billion as of February 2024, has fallen victim to a cyber attack led by the Anonymous Collective. This attack is a retaliatory move against companies, including Agilite, AM General, BAE Systems, The Boeing Company, Caterpillar, Colt's Manufacturing Company, Day & Zimmermann, Elbit Systems, Emtan Karmiel, Flyer Defense, SpearUAV, ThyssenKrupp, and XTEND, accused of supplying weapons and military equipment to Israel.
- Noname's Cyber Offensive Against Finland: Targeting the internet infrastructure of Finland, the threat group known as "noname" is orchestrating a joint attack, involving prominent entities in cyber warfare such as The National Cyber Army, 22C, PHOENIX, Federal Legion, UserSec, CyberDragon, and NETWORK (15). This ongoing campaign aims to disrupt Finland's online services and networks.
- Anonymous Sudan's Warning to UAE: In a significant development, FlyDubai, a major UAE-based airline, has been targeted in a cyber-attack by the threat group Anonymous Sudan. The assailants aimed at the airline's digital infrastructure, successfully disrupting critical components and causing a complete network outage. This attack resulted in the entire FlyDubai network being rendered inaccessible, including essential systems such as reservation and booking services, impacting users' ability to book flights. Anonymous Sudan has claimed responsibility for the attack, attributing it to the UAE's support for the genocidal actions of the Rapid Support Forces in Sudan. The group issues a warning, asserting that attacks on the UAE will persist until their demands are met. They acknowledge any damage to FlyDubai's systems as collateral damage within their broader campaign. This cyber incident has severely impacted FlyDubai's operations, emphasizing the susceptibility of critical infrastructure to cyber threats and highlighting the potential consequences of geopolitical tensions on digital systems.
Conclusion
In the past week, cyber threats persisted despite unexpected shifts, making law firms the most breached entities alongside consistent targeting of the manufacturing sector. Lockbit3 maintained its status as a major threat, while companies with 51-200 employees faced substantial risks. The United States led with 57.63% of breaches, emphasizing global cybersecurity collaboration. Industries like Manufacturing, Legal Services, and Construction faced significant threats, indicating the need for adaptive security measures. Ongoing dark web threats, including breaches in major US energy companies and cyber assaults by Anonymous Sudan, underscored the persistent and escalating nature of cyber risks with geopolitical implications. These events highlight the urgency for robust cybersecurity measures and global cooperation in an increasingly complex digital landscape.
About Foresiet!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


June 7, 2024, 7:02 p.m.

May 23, 2024, 8:02 p.m.