Inside the Black Basta Arsenal: A Deep Dive into the Tools Fueling Their 2024 Ransomware Campaigns

Here's a closer look at one such advanced malware employed with tools by Black Basta—to name a few, Zbot, DarkGate, and customer-designed payloads on order as well—and how these latter help in extracting data coupled with sustaining unauthorized access at some distance.
Introduction
Black Basta is a pretty advanced ransomware group active since back in 2022. Initially, the group targeted valued industries such as healthcare, finance, and manufacturing. However, by 2024, the same Black Basta had morphed into something else; perfecting the techniques with much more complicated tools and more intricate social engineering tactics. It has considered the recent activities that the group has undertaken, common tactics they used; emerging strategies that surfaced in their phase as they transitioned to 2024.
Overview of Black Basta
Black Basta is the evolution into the main tool of success. The gang's activities have sprawled all over the globe, leading to ransomware-based attacks while heavily using advanced tools for malware sophistication. In the year 2024, this group accelerated its attacks based on sophisticated phishing tactics along with cutting-edge social engineering techniques for the exploitation of corporate networks.
Shows blackbasta’s underground target victim listing
Shows Black Basta's underground target, which is a login form for a chat service hosted on the dark web.
The areas they value the targets are the healthcare sector, government institutions, and financial organizations due to the sensitive data they are dealing with. These sectors are the hot targets because of what they deal with.
Recent Activities and Tactics (2024)
Black Basta activities in 2024 have been much more sophisticated, subtle, and productive means of attacks. The most high-profile tactics realized this year include the following:
- Microsoft Teams Exploitation
Black Basta had to turn to Microsoft Teams in October 2024, to evade phishing. It targeted corporate IT help desks with phishing of employees who downloaded malware-infested applications, such as Zbot and DarkGate. The phishing used QR codes and direct links to the compromised software to gain access to the corporate networks. - Advanced Social Engineering
The social engineering of the Black Basta had been far enhanced. This gang, on several occasions, sent its spam to load in the employee's mail inbox with a fully filled message. These direct chat modules were newly released in 2024 and made their appearance dressed up as legit staff of the help desk. With this, it further gained their confidence by easing access privilege escalation through networks which they previously compromised. - Payloads Deployed
Continued using mixed malware with stolen files with sensitive information and malware with remote access control such as:- Zbot: This is a type of banking Trojan malware mainly used to steal login credentials of financial systems.
- DarkGate: Extremely versatile malware tool enabling one to gain remote control and exfiltrate data.
- Custom Malware: Tailor-made towards evading detection systems; consequently, this will ensure continuous access to victim networks.
Tools Used by Black Basta Ransomware for Attack Phases
Black Basta uses authentic as well as malignant tools to perpetrate their attacks. They ensure the attackers will first arrive and secure a foothold in the network before ex-filtrating sensitive data out of the network.
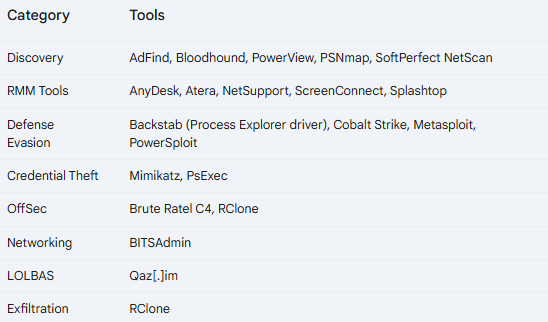
Remote Access Tools
Black Basta uses AnyDesk, Quick Assist, and ScreenConnect as part of the tools for unauthorized access and control of the victim's system. Thus, persistence connection and network manipulation from within will be supported by the remote access tools.
Post-Exploitation Frameworks
Once the target system is compromised, Black Basta uses post-exploitation tools like Cobalt Strike to perform lateral movement. In other words, attackers move within the network without having it identified; thus, this expands their reach areas and controls the environment.
Privilege Escalation
Black Basta uses Mimikatz and PowerShell scripts for the privilege. For instance, bypassing security controls, then it gains admin privileges on the compromised system before executing commands at a higher privilege level.
Data Exfiltration
The gang gets sensitive data through exfiltration via RClone, and WinSCP among other tools. With the tools, it takes its exfiltrated files out from the victim's network to the remote servers. That only means that information exfiltration capability of humongous volumes in record time without giving an alarm.
Execution Techniques
They are using various execution techniques that are mentioned above to the phishing emails and calls which unknowingly bring the victims to the execution of malicious payloads. Other than the above, they use public-facing systems for getting an initial foothold other than the propagation within the network. The tactics used helped them in expanding their attack surface quickly and efficiently.
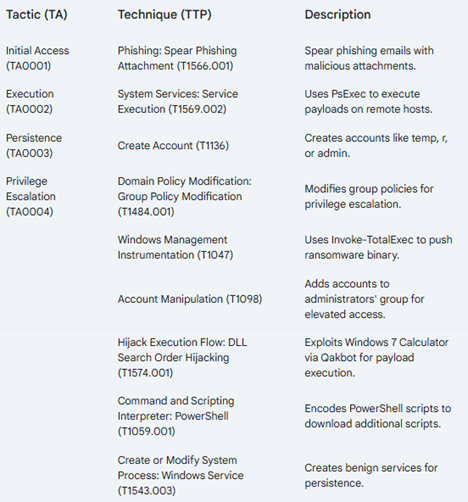
TTPs (Tactics, Techniques, and Procedures) of Black Basta Ransomware
Black Basta uses a wide range of techniques through several phases of the attack lifecycle, including spear phishing, executing payloads with PsExec, creating new accounts for access at elevated levels, and modifying system processes. They use PowerShell, DLL search order hijacking, and group policy modification to gain persistence and move up the privilege ladder.
Vulnerabilities in Popular Products (2024)
This includes some widely used products carrying several severe vulnerabilities, opening the door to attack organizations worldwide.
The simple YARA rule for detecting black Basta ransomware is given as:
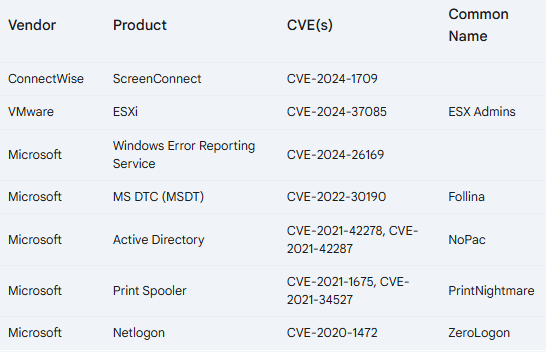
Simplified YARA Rule for Black Basta Ransomware Detection
In the following count only the single-byte sequence inside the file, but it puts greater emphasis on principal IOCs because of the minimum requirement concerning the size of the files for effective detection:
Black Basta Ransomware: Victims by Country (2024)
Black Basta has targeted the whole world in 2024, leaving the following per country reported incidents on record:
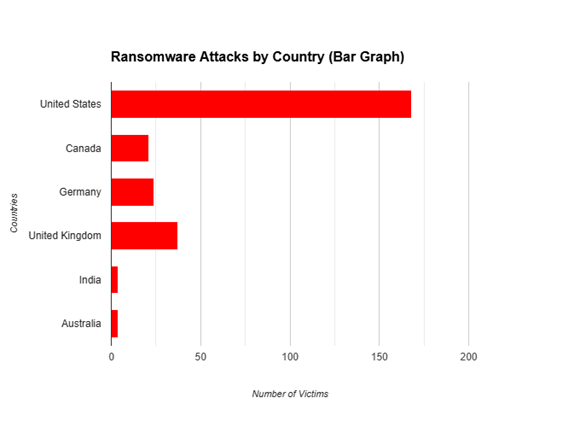
With this data, operations of Black Basta are confirmed running across geographies with a targeted approach on higher-value targets. For proper mitigation as well as critical analysis, these organizations need proactive defense and responses to incidents.
Mitigation Strategies
The dynamic tactics of Black Basta need to be prepared by the organizations before that. Some of the mitigation steps include the following:
- Employee Training: Employees must be trained in detecting phishing attacks, threats that might come from attachments or links not known before, etc.
- Network Segmentation: Keep your critical systems and data such that in case of a breach, the loss would be only minimal.
- Advanced Threat Detection: Use endpoint detection and response (EDR) solutions that detect suspicious activities and kill threats within seconds.
- Multi-Factor Authentication (MFA): To build up more of a security-oriented system, MFA must be used in all accounts considering any access which is made to systems containing sensitive information.
- Patching and Updates: Patch up and upgrade every system and application for minimal chances of exploitation by the attacker.
Conclusion
Black Basta comes out as nimble as well as technologically savvy in the cybercrime space for 2024. This can be claimed based on the fact that Microsoft Teams is used as a phishing tool along with the intelligent aspects of social engineering. Targeted malware, such as Zbot and DarkGate, among others, would put all organizations around the world at significant risk.
Businesses need to be much more attentive, invest in modern security solutions, and ensure that the staff of the business is better prepared to identify and respond to a cyber threat. Only all-inclusive and proactive measures can repel perhaps the rising threats of ransomware attacks by Black Basta and others.
About us!
Foresiet is the pioneering force in digital security solutions, offering the first integrated Digital Risk Protection SaaS platform. With 24x7x365 dark web monitoring and proactive threat intelligence, Foresiet safeguards against data breaches and intellectual property theft. Our robust suite includes brand protection, takedown services, and supply chain assessment, enhancing your organization's defense mechanisms. Attack surface management is a key component of our approach, ensuring comprehensive protection across all vulnerable points. Compliance is assured through adherence to ISO27001, NIST, GDPR, PCI, SOX, HIPAA, SAMA, CITC, and Third Party regulations. Additionally, our advanced antiphishing shield provides unparalleled protection against malicious emails. Trust Foresiet to empower your organization to navigate the digital landscape securely and confidently.
Protect your brand, reputation, data, and systems with Foresiet's Integrated Digital Risk Platform. 24/7/365 threat monitoring for total peace of mind.


